How to Detect a Keylogger on iPhone or Mac: A Comprehensive Guide
Apple makes some of the most secure devices. Hence it doesn’t come as a surprise that it’s difficult to install a keylogger on the iPhone unless the device is jailbroken or the person had physical access to it.
iPhones are known to be hard to hack, but there are ways to unlock iPhone passcode and get access to private information. If you’re worried about someone having installed a keylogger on your phone then worry not, we have covered some great tips on how to detect a keylogger on iPhone.
| Read also: How to Detect a Keylogger on Android
🥇 Use an Antivirus Software
🥈 Use an Anti-Malware Program
🥉 Use Little Snitch
Can You Put Spyware on an iPhone?
Yes, it is possible to put spying software on any phone, including an iPhone. Keyloggers and other spyware tools are designed to run silently on your device and stay hidden while reading your text messages and other files. This is why it is hard to scan the iPhone for spyware.
Warning Signs: How to Know If a Keylogger Is Installed
Here are some warning signs that can help you know if a keylogger has been installed on your phone:
- The battery may begin to heat up even when the phone is not in use. This happens because the keylogger is at work even when you’re not using the phone. Plus, phones with spyware and other such software often also take longer to charge due to the same reason.
- Keep an eye on how much data you’re using, especially when your phone isn’t actively being used. High volumes of data indicate the presence of hidden tools sending and receiving information.
- If your phone is suddenly hanging a lot, then it might be due to the presence of a keylogger. These software ‘read’ apps and can cause them to crash or get slow.
- Do you hear background noise when you’re on the phone? It might be due to a keylogger installed on the device.
How to Detect a Keylogger on an iPhone
Use an Antivirus Software
Using good antivirus software is possibly the best way to detect a keylogger on an iPhone. It regularly scans your device to detect keyloggers that are often present on your device without you knowing about them. Further, they also usually offer what’s known as keystroke protection, which prevents a hacker from accessing your keystrokes. This goes a long way in keeping all your data safe.
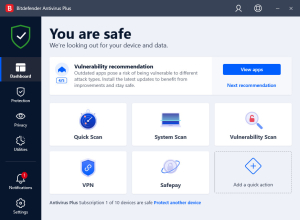
Use an Anti Malware Tool
Just like computers, mobile devices can get hacked or attacked as well. This is why there is no shortage of anti-malware or anti-keylogger tools on the market. You will find several apps designed to protect your device and delete all unwanted applications, including apps that stay hidden.
One of such anti-malware programs is EtreCheck.
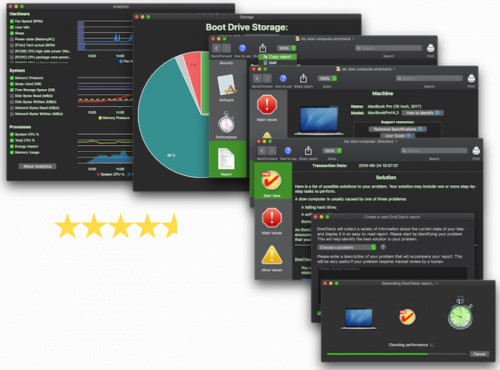
It was primarily marked as a Mac keylogger detector. With its help, you can detect serious problems on your Mac, remove annoying adware and just see what your device is doing on the side. Its reports protect your personal information when posted online and make no changes without your consent.
EtreCheck doesn’t require the phone owner to perform any manual task. All you need to do is to download > install > run the software.
Install Little Snitch
Little Snitch is a tool designed to make ‘invisible visible.’ With this app, you will be able to see what data is being sent and received through your device.
It can be set to send alerts in case an unauthorized or unsafe connection is identified.
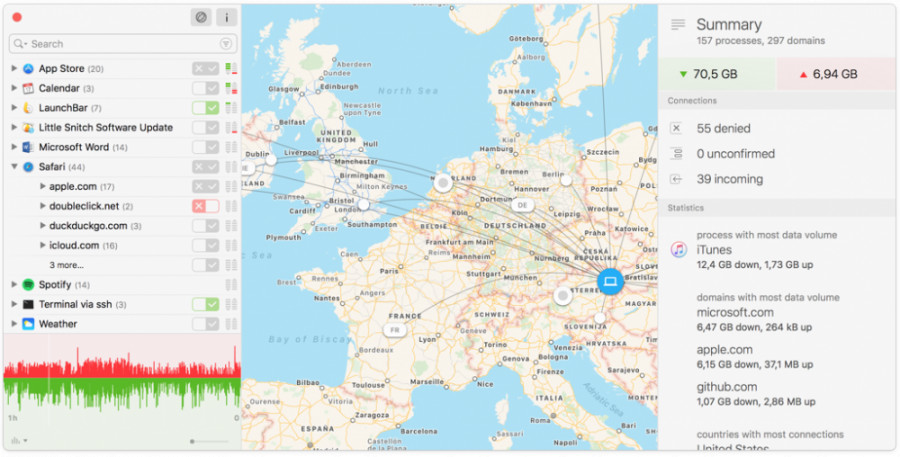
The app offers real-time data and can be set to work in silent mode. A look at detailed charts will help you identify if unauthorize information is being sent or received from your device.
While it cannot delete these apps on your behalf, it can be used to protect your social media account and text messages from intruders.
Make Use of Two-Factor Authentication (2FA)
Two-factor authentication is a technique used to prevent unauthorized access to an account or device. Once you have 2FA enabled on your device, hackers will not be able to access your accounts even if they have the login details.
2FA provides a second layer of security. If you have this feature enabled, anyone who tries to access your account will have to bypass a verification test even if they have the right password. The second verification test is usually in the form of a code that’s sent to your registered mobile number or email.
Even if someone has installed a keylogger on your device, the person will only be able to know your email and password and not the code until you type it. Since these codes become useless in a few minutes, the risk of getting hacked dramatically reduces.
2FA can help you detect the presence of a keylogger. If you get a code without trying to login, then it means someone’s trying to access your account.
Search for the Cydia App
If you find apps that you never installed on your device, then it might be an indication of a compromised phone. The presence of Cydia is a significant sign. It’s a package manager used to jailbreak your iOS device.
The problem with the Cydia app is that it can remain hidden on the device. You might not be able to unhide a keylogger, but you can try to unhide Cydia by going to Safari and opening “Cydia://”.
Install Oversight
Oversight was is developed to notify you whenever the camera on your device turns on. This is important because hackers can hack your camera remotely and keep an eye on your surroundings. Such instances are not typical and can result in the invasion of privacy and other such issues.

Some experts argue that placing tape over the camera is the best option to stay protected, but it might not be a feasible choice.
Installing Oversight and other such apps can do the trick. It will let you know if there’s a keylogger or spyware on your device. You can then take steps to get rid of such tools.
Check for Available Space
Keyloggers do not take a lot of space, yet paying attention to this factor can help you figure out if a keylogger is installed on your device.
To check storage:
- Go to Settings
- Click on General


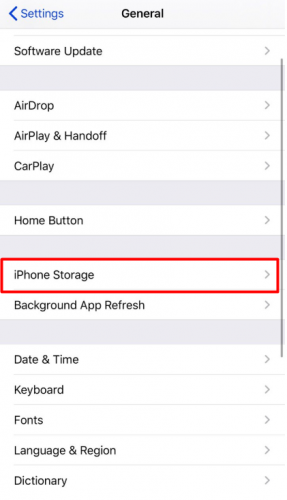
- Choose iPhone Storage

- The screen will display used and unused space. You will be able to see most of the installed apps.
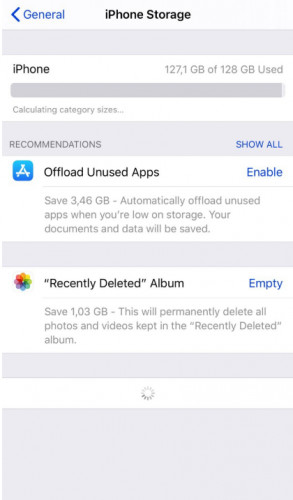

iPhone keyloggers may not appear here since they work in stealth, but you might be able to detect one by paying attention to how much space is available on your device.
How to Remove Spyware from Your iOS
Now that you know your device has been compromised, It’s time to protect your data. In addition to installing antivirus and enabling 2FA, you should:
Change Your Login Details
If someone already has access to your password and email, then make a move and change all your login details.
For additional safety, you can make a new email. Also, avoid using the same email and passwords for multiple accounts.
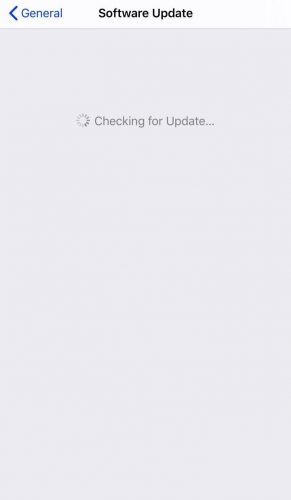
Update the Operating System
iOS is secure and reliable. You must, however, keep it updated to enjoy the latest security. Apple is known to release patches to protect against the latest hacks and attacks. The phone can be set to update automatically.
If not, you can perform manual updates:
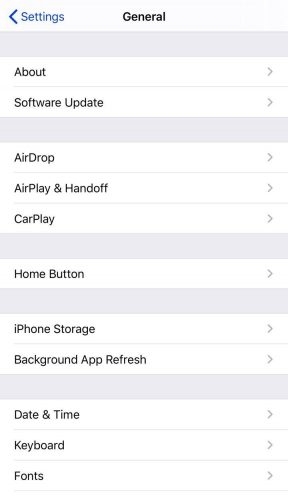
- Go to Settings



- Select General



- Choose Software Update

- Download and install the latest update (if available).

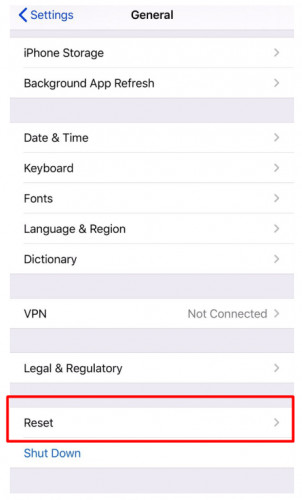
Factory Reset Your Device
While it’s the last option, it might be your only choice if nothing seems to work. This option will remove all the data stored on your device, and you will get an empty device.
- Go to Settings > General
- Scroll down and choose Reset

- Сhoose Reset All Settings
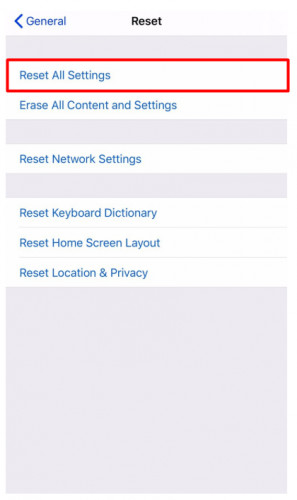

If resetting your device fails as well, then it’s time to get your hands on a new iPhone.
Yes I was hacked deplorable during a divorce. He disabled car thru an app or from his phone. Tried to set me up for numerous things through geofencing and gps. Then he used words from search bar as testimony in a trial. Tortured me 24 hours with families help and the law refused to help. He tore up a couple phones by locking them n burning them p some way. He put me on emails that he used like family locator. He was in WiFi cause jumped on each device. Is there any evidence anywhere. Please help me get this stopped.
You have to talk to a lawyer about this.
My ex husband is doing something similar to his new soon to be ex wife. She says things keep disappearing from her from her phone, like pictures of proof that he was cheating keep getting removed. She has a new phone. What should I advise her to do? I’ve told her to change her passwords to EVERYTHING. Get new email addresses. That’s all I can think off.
Install anti-spying software and/or an anti-virus, if it’s an Android, activate Google Play Protect. Make sure her iCloud/Google Play info (password + secret question) is changed and also don’t forget to activate 2FA Authentication.
Same issues.
It’s irresponsible and immoral to create apps specifically intended for malicious use. The developers should be held legally responsible for damages.
Hello
I am being hacked unmercifully. Hacked every account to include PayPal. Knows my doctor information for all of my licensure. Stole manuscripts for my books and my book covers. I am on administrative leave from work because they got into my work computer. Rigged my phone so that if I call the credit bureaus their number pops up as the contact information. Has my email going to an account that they locked me out of. Hacked into my payroll account. It goes on and on. Now they have moved to my husband. I don’t know what to do. When I close an account they open it back up. Bypassed all of by 2fa and biometrics to include my face/iris. I am at a loss
Hey Tracie, have you tried doing the following?
1) reinstall your operating system on your computer;
2) factory reset your phone;
3) create new accounts (iCloud, Google, whatever, … all of them);
4) install an anti-virus and a firewall on your computer;
5) install an anti-virus on your phone;
6) change your secret questions for ALL of your accounts, write it down on a paper in case your forget and hide it somewhere safe, do not store it digitally;
7) generate strong passwords with numbers, letters, special symbols and caps of about 12-15 characters;
8) use 2FA.
This is bulletproof. No way on earth anyone will be able to get to you then 🙂
My exneighbors have been hacking me going on five years. They sre in everything. No matter how many emails I change, passwords, phones android, iphones, sim cards, IMEIs, passwords, Phone numbers (which makes me look bad) email on gmail, icloud, my ex job at a hospital, my current job for a transport company, company, my modems that I change like my underwear, they even locked ne out of gmail and im in recovery with my work gmail currently, my landline connected to my modem, comes in my home through attic like he did in old house which firewall didn’t go all the way and it took me three years to figure out Now I cant figure out how? They removed a copy of my new house deed from my house. I got a replacement. I moved a year and a half called police and they cant prove anything. They control my security cameras no matter what I had. Arlo, ADT, Comcast. They know my personal data and like the sadistic sociopaths that they are they play victim when accused and confronted by law enforcement. Two against one, they claim Im crazy when they are bullies snd hide their misdeeds from everyone. Install keyloggers, get in my house when Im not not home, I change keys. Moved. No one does anything. When I had pictures on my hunting camera they remotely deleted them with Microsoft extensions on my chrome book that he made himself an administrator on. How do I stop these people and protect myself once and for all? Im not doing this dance for five years with them! It sounds unbelievable! I couldn’t make this stuff up!!!!
Do you use a vpn? Have you changed your SSDI name and password to a really long password using unusual symbols, uppercase, lower case, numbers and do not use a word or phrase. Make it like 16 characters. Regarding vpn, NordVPN is good and worth buying. You can put it on your phone and computers.
Freeze you credit. Go to all three credit bureau’s websites. Don’t lose pins! This is very important for everyone to do. I don’t know how old you are but I’d also set up your social security account online and then add the 2 step verification, plus they have a way to add more security. Go to the security section. Add all security measures. If you don’t set up your account, someone can try to in your name and file under you. Even if you’re in your 50’s, I’d do this.
I’d call all my banks and utilities and put grid alerts on them.
Add a good malware/spyware, etc app to your phone and computers. Make sure to set up scheduled scams and keep the software updated.
Get a password manager like LastPass and Change all your passwords to very long passwords, using the credentials I listed above. Do not use the same passwords. If you’re on social media, go into security settings in all apps and make sure to turn off any settings that share info. Facebook is awful! Plus, info gets stolen from them all the time. Pretty much all your pictures and posts have probably already been stolen from the 2016 incident and the recent police by. It took me hours to secure my phone. Use Duck Duck Go as your browser. It’s best for privacy.
Always use two-step verification on ALL accounts that allow it. This is one of the biggest thing people fail to do. That, and getting a vpn.
Hope that helps some.
My wife’s iPhone is being hacked/tracked somehow. WhatsApp, Snapchat, contacts have all even compromised, ie changed, updated, Avatars added. Her icloud emails take up to 24 hours to be received. She is convinced that there is some sort of keystroke device monitoring her every move. Links to unknown ip addresses and URLs (including porn, developer sites) are showing up.
We have used network scanners (such as FING), that show hundred of addresses have been connected to our router, addresses that mean nothing to us. This is all very worrying.
Can you suggest anything please?
Thank you.
Fing won’t do much, it’s normal that a lot of addresses are “connected” since you’re surfing the web. There’s a constant back and forth between you and servers.
The problem might be that she uses the same password on all accounts and these have been leaked somewhere. Try checking out haveibeenpwned.com to see what’s up.
Hi,
Would you consider doing some consulting work are use multiple iPhones and iPad and it appears I need to get a laptop. They really crippled my business or stealing clients they stalled my business model they see my text my emails they finish writing them make it so I cannot email or call certain important people and it’s all related to people that are helping me attorneys or CEOs of companies that they want to ruin my relationship with
Certain business associates have hacked me to the extreme it’s too long to write but it’s only happened since I did an audit and caught Them
This email address, as well as my others, have been compromised by them and then I got my fifth iPhone I carry three different numbers now and email addresses and within a week they had that one too.
So maybe if you’re interested we could talk via signal or WhatsApp about some consulting work for you. One of the business associates there a collective gang said it’s his life‘s mission now to ruin my life
Steve
Hey Stephen, that sounds bad, but unfortunately, we don’t offer any services as of now. We’re trying to write about the latest information on phone trackers, maybe you have a specific request we could process and make a case out of it?
There’s actually no anti-keylogging/phishing/spyware apps (via the iOS App Store) to install and help find any key loggers that exist on an iPhone, it seems to be some Apple limitation/restriction. I’ve checked all the ones mentioned here and they only allow that for computers, not mobiles like iPad or iPhone. They all do the same basic stuff- VPN, secure email, data breach checks via email, etc etc. Basic stuff, nothing as advanced as scans and whatnot like a computer. It’s too bad.
Unless I’m wrong (which I’d love to be!) and you can point me to specific ones that can show a user if there’s loggers, spyware or adware installed and can wipe them out, unfortunately.
Hey Darren, there simply is no logical way to guarantee the absence of keylogging software. There are only ways to determine the presence of certain, known key loggers; and even if you were to confirm the presence of a well-known one, it could have been installed in an effort to distract you from the presence of some lesser-known one more difficult to detect or eliminate.
We’ll try to create an app that detects mSpy and other keyloggers in the near future.
I had my apple account hacked. They bought something using it and changed the password to lock me out. The password was 25 characters long and the 2FA was Touch ID for the purchase. Apple declined to explain how this was possible.
Is backboardd.wakeup_resource file a jailbreak app and how do I get rid of it! Last night I got signed out of my iCloud account and signed in under a Game Center! I lost all my contacts and emails, I installed Avast and it won’t scan my phone and when I was typing in my email an email unknown to appeared! I think the hacker got through to my phone through the Gettr app and they have been absolutely no help! Everytime I download that app a new backboardd file opens in my Analytics log!