How to Hack a Twitter Account Easily [Top Methods in 2025]
There are more than million Twitter accounts. And Twitter users have a deep concern about the security risks flowing from serious data security lapses. A San Francisco company signed a multi-million dollar deal with Twitter to provide enhanced privacy protection program.
So, yes, Twitter is one of the most popular platforms in the world, with millions of active users. However, with the increasing use of social media, the risk of hacking and targeted phishing has become a major concern for many users. But you can use it for your profit. If you are an advanced Twitter user.
Hacking Twitter is not an easy task, but it can be done if you know the right tools and techniques. In this guide, we will walk you through the process of how you can get hacked account step by step. So you can understand how it works and how to protect yourself from potential attacks.
So, if you’re ready to learn how to hack a Twitter account, let’s get started!
Twitter Spy Apps: How to Hack Twitter Account?
For many years Twitter has been a platform for individuals to criticize oppressive governments and hold them accountable for their actions, even at the risk of having their identities exposed. But nobody can feel safe in this world 🤷♂️
Twitter reported that it has appointed Israeli security researcher Alon Gal as its new Chief Technology Officer, bringing his extensive experience in cybersecurity to the company. But does Twitter really have poor cybersecurity defences?

Example. In August 2019, hackers breached the account belonging to Twitter co founder Jack Dorsey. The malicious hackers flooded Dorsey’s account with racist remarks and other uncouth comments relating to the Holocaust. Company’s co founder Dorsey is not the only public figure who has fallen prey to such attacks. The profile of Rudy Giuliani, who serves as the attorney for Donald Trump, was also compromised. A security incident impacting accounts has been detected, and they were taking immediate measures to mitigate the potential damage.
Finally, Twitter entered into a consent agreement with the Federal Trade Commission over allegations that the company misled consumers about the extent to which it protects the security and privacy of their personal information.
Twitter’s weak cybersecurity defenses have been frequently denounced by security , who have pointed out numerous hacked accounts. The social media risks are related:
- to way of getting verified accounts;
- to password protected accounts;
- to Twitter dedicated email address;
- to information security.
So, the platform has reported serious data security lapses, including the exposure of millions of Twitter accounts’ passwords and personal emails linked to those accounts. By the way, we know that there are a lot of fake accounts, serious security risks, especially a risk of being hacked. For example, Twitter removed thousands of fake accounts for spreading misinformation about the COVID-19 pandemic. So, security experts conclude about poor cybersecurity defenses of personal details there.
A security researcher who wishes to remain anonymous has identified various security risks flowing from the ability of multiple accounts to access the site anonymously. One of the biggest risks on Twitter is the spread of false information, with many users falsely claiming things without evidence or proof.
But we should mention that Twitter employees have been working hard to remove fake accounts from the platform in recent years to maintain its credibility.

What Are Twitter Spy Apps?
Twitter spy apps are tools that allow users to monitor someone’s account without their knowledge. They allow us to get access to password protected accounts, Twitter dedicated email address, personal emails linked with this social media. A security researcher discovered a vulnerability that allowed access to other accounts on the site anonymously.
These apps can provide a range of features, including access to direct messages, tweets, and other activities on the account. They can be used for personal or professional purposes, such as to keep an eye on a child’s online activity or to monitor the social media presence of a business competitor.
However, it’s important to note that using spy apps to access someone’s Twitter account without their consent may violate ethical and legal boundaries. It’s essential to consider the potential consequences and seek legal advice before using these types of apps.
If you’re interested in monitoring app activity, check out some of the top Twitter spy apps and start tracking today!
Cocospy: The Optimal Solution for Twitter Accounts Hack
Twitter employees must comply with the terms of the company’s consent agreement to ensure that user privacy is protected. But that does not mean that we cannot hack this social media. One of possible ways to do this is Cocospy using.
Cocospy is Twitter hacking software that records activity on the target device. The software is compatible with Android and iOS devices. However, Cocospy can do much more than just spying on Twitter. You can also use it to access Snapchat and other social media accounts, track the target’s location, and even keep track of their messages and calls.
It runs silently in the background, recording keystrokes in a manner that the phone user won’t notice.
Cocospy Features
Here are some features of Cocospy that include Twitter:
- Social Media Monitoring;
- Keylogger;
- Call Monitoring;
- GPS Tracking;
- Browser History Monitoring.
Cocospy Pros & Cons
Here are some pros and cons of using Cocospy:
Pros
- Easy to use
- No need to jailbreak or root the phone
- Comprehensive tracking features
- Remote access
- Stealth mode
Cons
- Expensive
- Limited compatibility
- No live support
There is also especially a risk of misuse: Like any monitoring app, Cocospy could be misused if it falls into the wrong hands. It is important for users to use the app responsibly and ethically. But despite of limited compatibility, Cocospy is one of the most popular iPhone spy apps.
How to Install Cocospy?
To set up Cocospy and start monitoring a target device, follow these steps:
Step 1: Go to your browser and register for Cocospy. Here you use your target’s email address and credentials to complete the step.
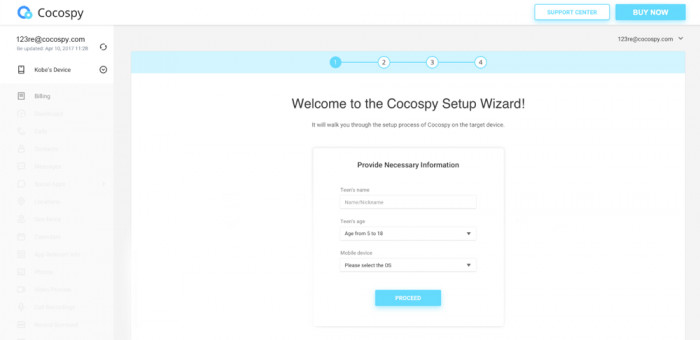
Step 2: Continue the setup process.
Here, you add the phones for monitoring. During this step, rename the cell phone that is being monitored for easy identification of the device monitoring list. Also, select the operating system of the target phone appropriately.
Note: If you have the target device, the process will take a few minutes.
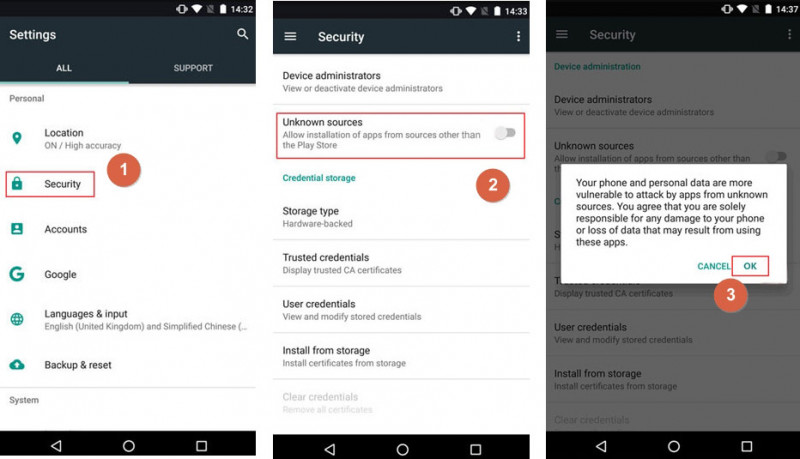
Step 3: Enable download from unknown sources from the security settings.
Navigate to Security “Settings” and tap on “Lock screen and security” to choose this preference.
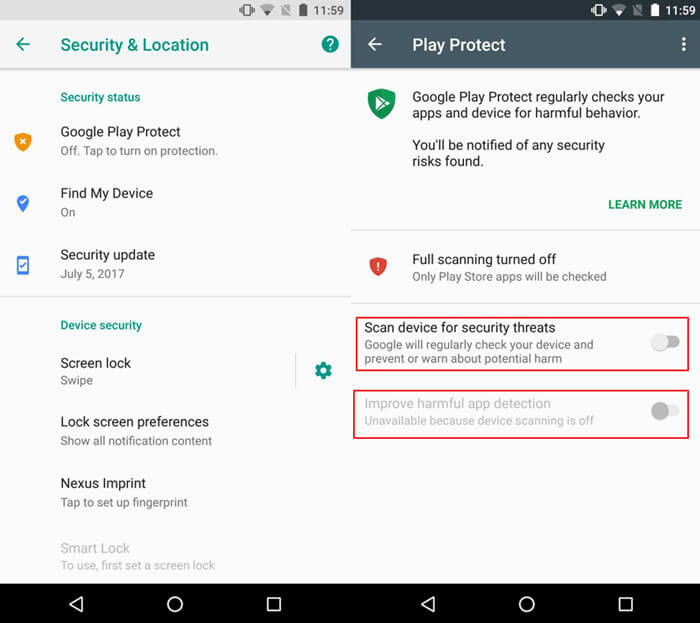
Step 4: Still on security settings, disable “Improve harmful app detection” and “Scan device for security threats” on Google Protect.
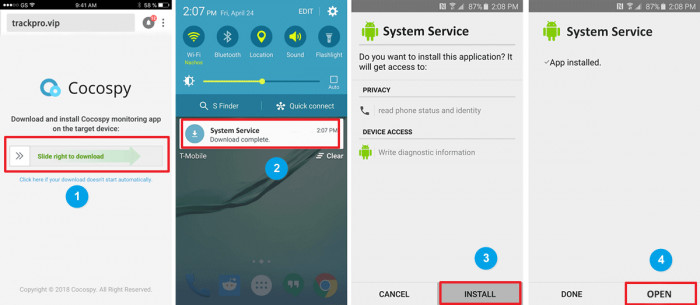
Step 5: Install Cocospy.
With a download link from the setup page, begin your download. Open the notification of successful download and installation.
Step 6: Agree to Cocospy terms and conditions then sign in with the email address and Twitter credentials.
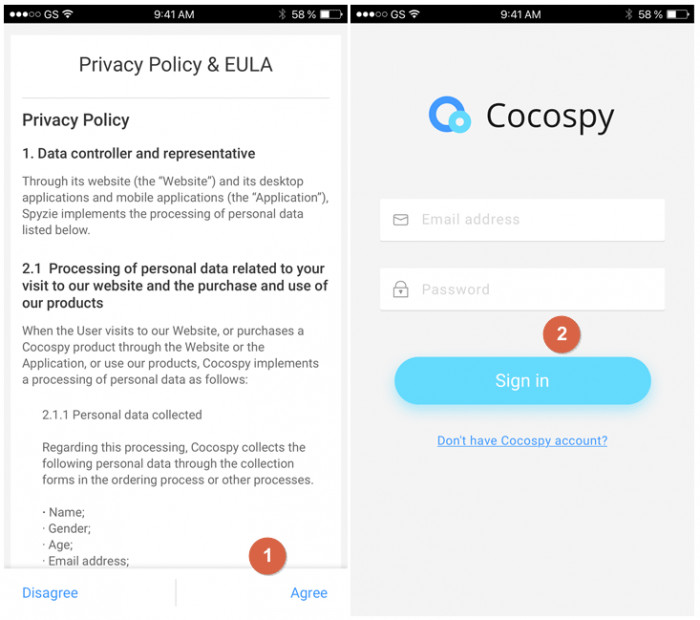
Step 7: Next, follow the wizard settings to set the app on stealth mode. Any time you want to evoke the app, dial **001**. When choosing the Twitter feature, keep in mind that no jailbreak is required.
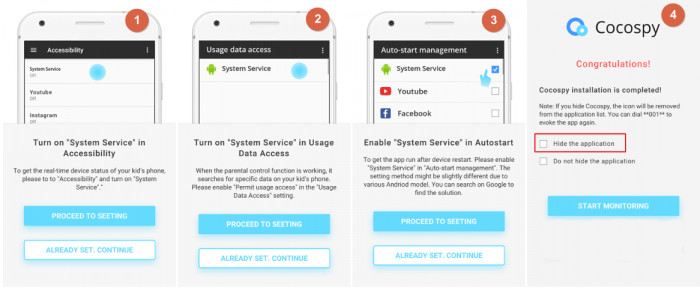
Step 8: Finish Installation and start tracking the target devices. You can do anything and everything – hack their Gmail account and even snoop on their Instagram.
uMobix: The Convenient Way to Hack Someone’s Twitter Account
Do you also want to keep tabs on someone’s Twitter account? Whether it’s for personal reasons or for investigative purposes, uMobix is a convenient way to hack into someone’s account. With its user-friendly interface and powerful features, uMobix is an all-in-one solution for monitoring someone’s social media activity, including Twitter. In this article, we’ll explore the benefits of uMobix and how it can help you gain access to someone’s Twitter account.
uMobix Features
Here are some of the most noteworthy ones:
- Call and SMS monitoring;
- Social media monitoring;
- GPS tracking;
- Keylogger functionality;
- Web browsing history tracking;
- App usage monitoring;
- Remote control of the target device;
- Email monitoring.
uMobix Pros & Cons
Pros
- Easy to install and use, even for non-technical users
- Allows you to track a variety of data, including call logs, messages, social media, and more
- Offers a comprehensive dashboard for quick access to all the information you need
- Provides detailed reports on the target’s activity, making it easy to identify potential risks or issues
- Works in stealth mode, so you can monitor the target’s activity without being detected
Cons
- Limited compatibility
- Rooting requirement
- No trial version
How to Install uMobix?
The uMobix installation is very close to Cocospy. Here’s a step-by-step guide on how to install uMobix:
- Purchase a subscription.
- Create an account.
- Select the target device.
- Install uMobix on the target device.
- Activate the app.
- Start monitoring.
- Customize settings.
That’s it! With uMobix, monitoring a target device is a straightforward process that doesn’t require any technical knowledge.
How to Hack into a Twitter Account Without Coding: Twitter Hacker Pro
The hack appears to have allowed malicious hackers to numerous Twitter accounts compromised, as it does not require coding skills.
Twitter Hacker Pro is a user-friendly tool designed to provide a fast and free way to crack Twitter account passwords of your choice. The program has a singular objective, which is to enable average internet users to effortlessly crack Twitter account passwords with just one click.
However, there are concerns that the company misled regulators regarding the tool’s intended purpose and the potential risks associated with its use.
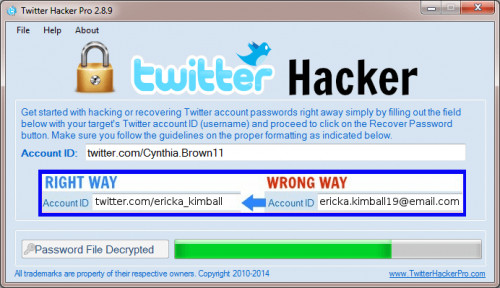
Twitter Hacker Pro app comes with two downloads – the software and malware software that’s easy-to-use.
Step 1: Download then install.
Step 2: Follow the screen prompts to proceed.
Step 3: Enter the login credentials for the target Twitter accounts. You may want to hack your spouses, kid’s or workers’ accounts.
Step 4: Allow the app to scoop information about the account. Soon you will receive the credentials that you can use to log into the target account.
This set of instructions involves using an app to hack into Twitter accounts by obtaining the login credentials. In addition, this method is outlined by the Israeli security researcher Alon Gal. If Twitter employees were to become aware of this activity, it would be imperative for them to immediately respond and address the serious security risks posed by such an app. Furthermore, the fact that personal emails are linked to these accounts only amplifies the severity of the situation. It is clear that by allowing such activities to occur, Twitter has violated its own security policies.
How to Hack a Twitter Account Online for Free
Beware of hastily signing up for free spy applications available online, as they do not always deliver on their promises of seamless Twitter hacking experiences. Instead, they often use targeted phishing tactics that rely on personal emails linked to Twitter account passwords.
While Twitter does offer paid options for account security, the platform has still seen numerous accounts compromised. Twitter has violated its users’ trust in the past by allowing hack appears falsely claiming to have access to million Twitter accounts.
Users should be cautious when prompted to enter personal information and passwords on third-party websites or applications, particularly those claiming to offer free hacking services. We have come across some free hacking options on the web for Twitter accounts, as well as for other accounts that require passwords.
These are some free Twitter hacking options we’ve found on the web. Proceed with caution:
Twithack
Twithack is a software tool designed to gain unauthorized access to Twitter accounts. This software claims to use sophisticated algorithms and techniques to bypass Twitter’s security measures and gain access to a user’s account. It is usually offered as a downloadable program that users can install on their computers.
Twithack is a free software that claims to hack a Twitter profile in seconds. However, we have tested the webpage and confirmed that it does not work as promised. It is crucial to note that attempting to use such programs could result in accounts compromised, as users enter sensitive information.
Here’s what you should do if you’d like to test it out for yourself.
Steps to use Twithack:
Follow these few steps to hack Twitter using Twithack:
- Go to their website on http://twithack.start-hacking.us/.
- Post your Twitter URL on the box provided after opening the link.
- Hack the email address and credentials linked to the Twitter account.
- Hit CONTINUE and wait for some minutes to get the target email and Twitter information.
Using Twithack may prompt users enter personal emails linked to the target Twitter account, which can compromise their security.
Twithack V2
Here is another free software that operates similarly to Twitthack, requiring no advanced IT knowledge to use for hacking Twitter accounts. However, as with the previous app, obtaining the target’s Twitter account data and credentials (keyword!) has proven difficult.
Here are the steps to use this tool while maintaining your anonymity on Twitter:
Step 1: Identify the username of the target user account.
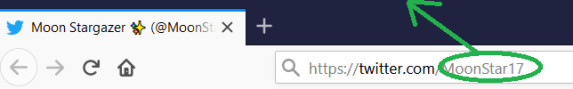
Step 2: Copy the user ID and paste on the social media hacker tool. Shortly, the credentials will show on the screen of the tool.
Step 3: Complete a short survey to confirm you are not a robot.
Step 4: Sign in to Twitter using the provided credentials.
How to Hack a Twitter Account without Download or Survey
Recent developments have highlighted Twitter’s poor cybersecurity defenses, which have led to data breaches and users’ identities being exposed. In 2020, Twitter employees were able to reset people’s passwords, granting them access to password-protected accounts.
This led to a formal investigation by the Federal Trade Commission, and the San Francisco company signed a consent decree that included updated data security commitments.
Password Reset
Twitter claimed to have auto-generated codes to reset passwords and prevent unauthorized access to accounts. However, a security researcher found that Twitter violated its data security commitments by allowing users to reset passwords through a phishing website.
To reset a password, you need the target’s personal email linked to their account. Twitter paid a $250,000 fine for misleading regulators. The Chief Technology Officer of Twitter has confirmed that the company is monitoring recent advancements and has updated version established of its data security commitments.
If your target uses Yahoo, you can read our guide on how to hack someone’s Yahoo. If you’d like to hack someone’s Gmail, we have an article about that too.
Now, let’s get back to the instructions:
- Firstly, navigate to the Twitter log in page.
- Now, you need to enter the target person’s phone number, email address, or Twitter username.
- Check the inbox to view the “password reset” email.
- You are now a hacker. Click the “reset password” link to reset the Twitter credentials then log in.
But falsely claiming to have accessed high-profile accounts could result in severe consequences, including a formal investigation by Twitter.
View Masked Passwords
Twitter violated its users’ privacy when it was discovered that a group of hackers managed to access high profile accounts and leave them vulnerable to scams. In the process, thousands of identities exposed, causing a huge uproar in the social media platform.
As a precautionary measure, Twitter anonymously encouraged its users to update their passwords and enable two-factor authentication. Moreover, Twitter paid a hefty amount to settle the legal dispute and to prevent any further breach of security.
To gain unauthorized access to Twitter, one of the easiest methods is to view masked credentials that are saved on the user’s browser. These credentials are typically denoted by asterisks (****) and can be viewed using a browser password checker.
Follow these steps to reveal masked credentials from a browser:
- Right-click from the Twitter password box on the browser.
- Select-Inspect Element to reach the developer console window.
- Tap on the type password option and change the existing credentials to text format.
Social Engineering is another method of finding Twitter credentials by yourself. The method uses trial and error to get the Twitter credentials where you know the email address used at registration.
It is a way that scammers use to gain admittance to Twitter credentials. It involves creating a fake Twitter website and email, and impersonating a Twitter employees to trick targets into revealing their login credentials. This is a complicated and time-consuming process, but if scammers are patient, they can make it work.
Social engineering uses psychology and research to scam targets. This method is a bit more complicated and time-consuming, but if you’re patient, you can make it work.
You should create a fake Twitter website that is a copy of the real website, a fake email that looks like it’s real, and find a Twitter employee whom you’d like to impersonate. Reach out to your target and tell them that someone is trying to hack their Twitter account. Then, tell them that you need to verify their identity by logging into their Twitter account.
Send over the link of your fake Twitter website to the target and have them enter the login credentials. When they do, you will receive their credentials, which you can then use to access their Twitter account.
How to Hack a Twitter Account with Programming
These methods are used by nerds, meaning you need a little more knowledge to deploy. Here we explore three options that include:
Phishing
Phishing uses spam messages directed at the target device, and once the owner opens the message, the vulnerability begins. Phishing refers the target to a fake webpage similar to that of the actual page hence requiring the user to log in to the target Twitter or to hack someone’s phone.
Other links will pose as fake sign-up pages that redirect you to the real fake page. The method echoes the actual Twitter page, and you won’t notice the difference in entering login information.
SIM Swap
Sim swap is also known as sim hacking. It is a method where the hacker replaces sim card phone numbers with the help of a service provider and consequently uses the replaced sim to gain access to a target Twitter. Jack Dorsey’s Twitter hacking happened through this method.
Brute-Force
Brute-force is similar to social media engineering, but it uses bots that attempt to log in to the targeted Twitter. The method makes trials using different combinations until it finds the real passwords.
How to Protect your Twitter Account from Being Hacked
Protect your Twitter from hacking by using these tips:
- Deploy Login Verification. Link your Twitter to your phone and ensure you activate phone verification for every login.
- Do not authorize third-party apps on your Twitter. Delink any third-party apps that gain access to your Twitter.
- Install genuine antivirus. Keep your phone and computer virus-free by installing genuine antivirus software that deletes malware.
- Use strong passwords. Paraphrases make right credentials. Include letters, characters, and numbers for extra strength. Avoid phone numbers.
- Authentic sign-in page. Only sign in using the real Twitter URL. https://Twitter.com/.
Can I Hack Twitter Anonymously?
Information security is a crucial aspect of our online lives. It’s important to stay up to date with the latest security measures and make sure that our information is protected. Recently, an updated version established for a popular platform was criticized by security researchers because the hack appears to be enabled. That means that it is possible to hack Twitter’s systems. This breach occurred because the platform failed to properly secure its users’ data. It’s also important to be aware of consent agreements when using various online services.
Some services may have hidden clauses that allow them to share your information without your knowledge or consent. It’s also important to note that there are people who falsely claim to be able to hack into accounts, and may lead you to a phishing website. However, there are also legitimate security researchers who can help identify and address vulnerabilities. These individuals can play an important role in helping to criticize oppressive governments and protect individuals from online threats.
We have also one more problem. Auto-generated code is often used to reset people’s passwords when they forget them. However, this process can pose an especially high risk if identities are exposed in the process. If a hacker gains access to the auto-generated code, they could potentially reset passwords for multiple user accounts and gain access to sensitive information.
To mitigate this risk, many companies use additional security measures such as two-factor authentication or CAPTCHAs. It is also important for users to use strong and unique passwords and to enable two-factor authentication whenever possible to further protect their accounts.
Conclusion
So, hacking a Twitter account can be done easily with the right tools and methods. While there are many options out there, Cocospy and uMobix stand out as reliable and effective solutions for accessing someone’s Twitter account without their knowledge. Both of these apps offer a range of features and benefits that make them worth considering, from their user-friendly interfaces to their stealthy operation.
Whether you’re trying to keep tabs on your child’s social media use or need to investigate a potential security threat, these tools can help you get the job done. With the right approach and a little bit of help from the experts, hacking a Twitter account can be a breeze.